Cybersecurity Plans: Top 4 Reasons To Have One In Place
Cybersecurity Plan | Managed IT | Network Security & Cybersecurity
According to Verizon’s 2022 Data Breach Investigations Report (DBIR), 86% of cybersecurity threats are financially motivated, outsiders cause 70% of data breaches, 45% of data breaches involve hacking, 22% are feature phishing or social engineering, and 17% involve a type of malware component.
Although there are quite a few different data breaches to consider, these statistics have increased significantly in the last two years. A solid cybersecurity plan can help any small to large-scale company face a cyberattack head-on if ever one does occur.
For over 20 years, LDI Connect has been working one-on-one with clients to optimize their cybersecurity solutions through our Managed IT service offerings. With cybersecurity attacks on the rise, it is of vital importance that every business has a solidified game-plan in place for when a data breach happens.
Within this article, we will first address what a cybersecurity plan is. Then we will dive into four primary reasons for implementing a cybersecurity plan and how it will allow your team to prepare for a cyber-attack.
Finally, we will go over a list of questions to ask your managed IT provider or pre-existing internal IT Department to update your pre-existing cybersecurity plan or create a new one. These questions will prepare you to have a productive conversation about your cybersecurity needs.
What is a Cybersecurity Plan?
A cybersecurity plan serves as a foundational document for your business. This written document will contain an outline of your business’s technology, processes, and overall incident management approach from end to end.
A cybersecurity plan acts as a comprehensive business roadmap for identifying, detecting, responding to, and mitigating any existing or potential risks linked to any given incident.
Most cybersecurity plans also include organizational charts to identify which team member is responsible for what is during a cybersecurity threat. A go-to cybersecurity plan is exceedingly helpful during urgent cybersecurity situations and training personnel on the game plan to follow should a problem arise.
Let us take a deeper look at why implementing a plan is so important.
What Are The Top 4 Reasons For Implementing A Cybersecurity Plan
Whether your business already has an operational cybersecurity plan or requires a new one, below is a list of four significant reasons why your business could use one.
1. Establishes A Cybersecurity Procedure
Implementing an organized cybersecurity procedure is similar to running a fire drill. Having a specific strategy in place so that employees know what to do if and when a cyberattack occurs helps mitigate the attack before it’s too late.
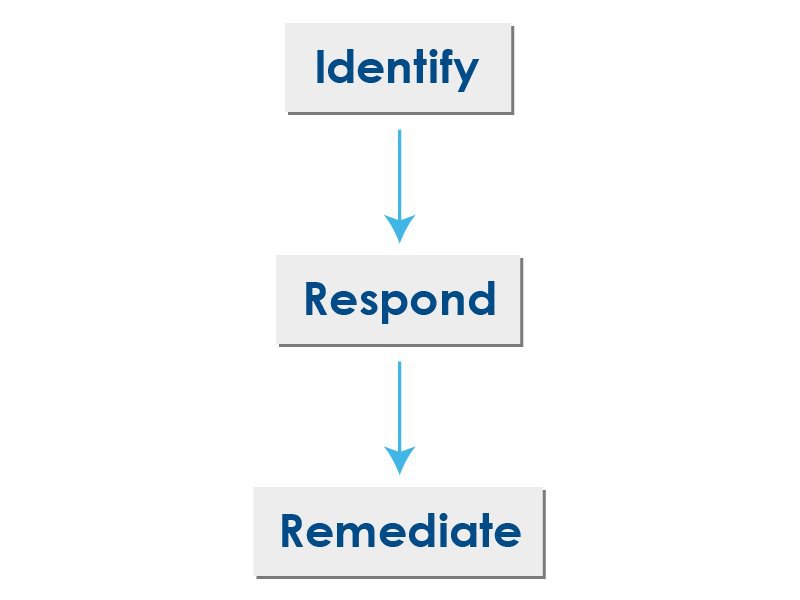 An organized cybersecurity procedure will include a step-by-step process. This process will identify potential risks, respond to them, and then finally remediate them entirely.
An organized cybersecurity procedure will include a step-by-step process. This process will identify potential risks, respond to them, and then finally remediate them entirely.
Identifying Risks
This process will require your team to define risks from past and current projects, document them, utilize risk identification tools and techniques, and create a Risk Checklist. A Risk Checklist ensures that common project risks do not get overlooked.
Several variables could lead to a data breach. However, having a proper risk identification strategy that includes the steps necessary to ensure no risks from the onset can be beneficial.
Responding To Risks
Building a separate process regarding an effective Cybersecurity Incident Response Plan is essential in setting up a cybersecurity attack plan.
First, identify the most critical data for your organization. Second, take steps to protect your most important data, which involves mapping your network environment and applications, keeping security patches current. Finally, establish a test procedure and schedule for testing your incident response plan for speed and efficiency.
Remediating Risks
Your business will be better off acting overly precautious than in denial about the potential risk from the onset. Setting up a risk mitigation process with your internal IT department or Managed IT Provider will be a necessity in your overarching cybersecurity plan.
Risk management isn’t always best taken care of internally; it may negatively affect events. Choosing a trusted Managed IT provider for facilitating risk management might be a better option for your business.
2. Incorporates A Cybersecurity Gap Analysis
A cybersecurity gap analysis can help determine what your business’s state of information security should be in the long run.
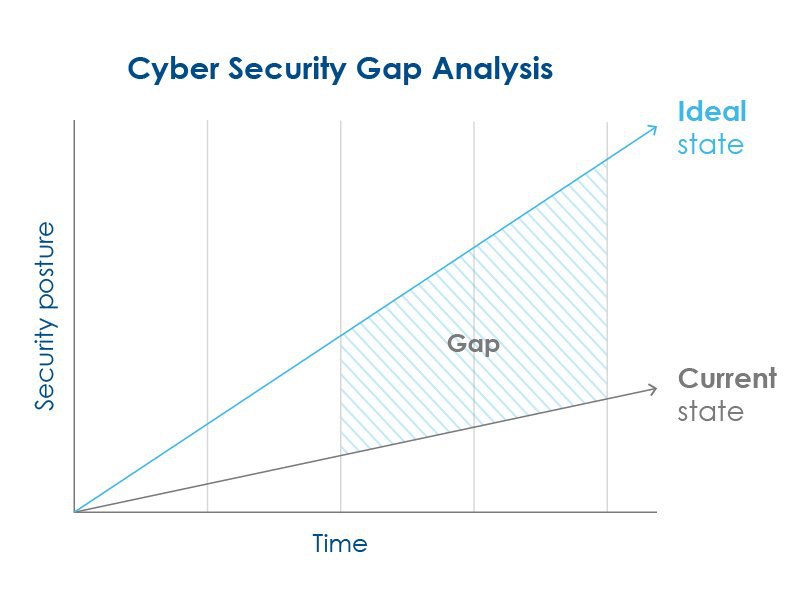
While the process of conducting gap analysis can contain many various stages, it simply requires your Managed IT provider or internal IT provider to routinely analyze and assess how secure your overall network or project may be.
Doing a partial security assessment and scheduling routine assessments with your chosen time is incredibly beneficial in keeping your business secure.
Analyzing your cybersecurity coverage gaps can help gauge your network or project as a whole. Getting a deeper look at what holes your business may be leaving open for cyber attackers to crawl into can help stop future cyberattacks.
3. Includes An Organizational Chart
Including an organizational chart in your cybersecurity plan is very helpful. An organizational chart shows your team who to go to during a cybersecurity threat. It can help mitigate any confusion before or after a cyberattack occurs.
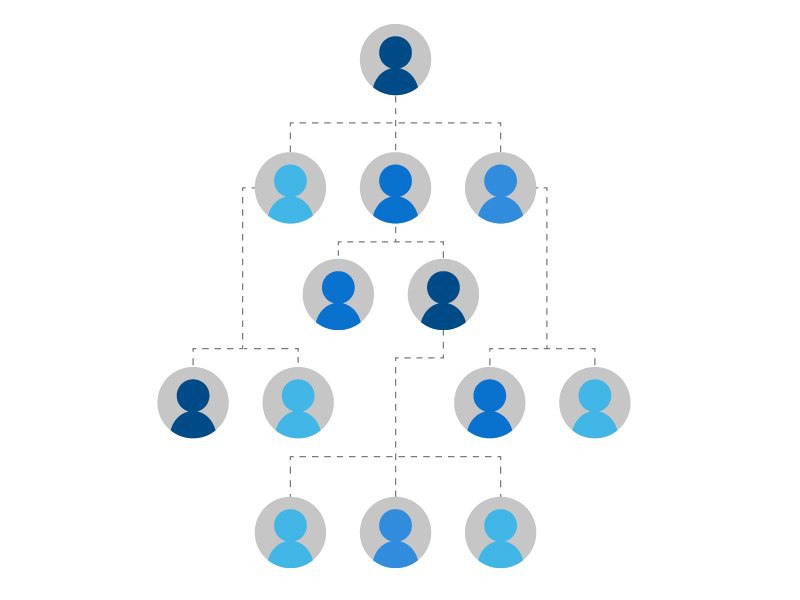
An organizational chart will drastically improve your team’s operations when it comes to solidifying a cybersecurity plan. It will also reduce the amount of time between identifying a plausible risk and reporting it.
4. Acts As a Training Manual
A thorough cybersecurity plan acts as a dual-purpose document. A cybersecurity plan must be easy to understand for new hires to learn. With security processes broken down for anyone to understand, your cybersecurity plan will act as an excellent training document.
Once your company has created a cybersecurity plan, the final step is to keep every employee and new hire abreast of this new cybersecurity procedure moving forward.
With a solid cybersecurity plan, every team member knows what the exact game-plan is to follow.
What questions should you ask about your plan?
Now that you have learned the different vital reasons why implementing a cybersecurity plan is essential for your business, it’s time to address how to implement one and what questions to ask.
Many Managed IT providers can help your team create a new cybersecurity plan from scratch or update a plan that you already have.
If outsourcing Managed IT services is not an option for your business, ensuring that your IT department knows how to implement one and what features to include is critical.
Once you have decided on what route to choose for your cybersecurity plan, coming up with a list of questions to ask can help you feel prepared to take the next step.
Here is a list of questions that we recommend you ask either your Managed IT provider or your existing IT Department regarding your cybersecurity plan:
Do I have a cybersecurity plan in place, and what does it consist of?
Evaluate your current cybersecurity strategy and find out if you have one in place. You can do this by speaking directly with your internal IT department or managed IT department on what your plan has been so far and what it’s made up of.
What are my current defenses, and what is my current cybersecurity posture?
Once you’ve figured out whether you have a plan to begin with, and what it consists of, it’s best to look for your current defenses set up for when a data breach might occur.
Knowing your defense line for when this happens will help you address whether it has worked for you in the past and whether you would like to implement the same defenses moving forward.
How does my business measure up to the recommended standard of cybersecurity?
Knowing whether your cybersecurity plan meets the recommended standard can help you assess how much work needs to go into crafting a brand new cybersecurity plan.
What does the process of creating a cybersecurity plan look like?
A cybersecurity plan has various features that can help your team mitigate cyber threats; making sure your company is aware of what needs to be included is crucial.
This process may involve a medium-sized team of people or just a few managers working closely with a Managed IT provider or your company’s IT Department. It helps to know the process before signing up for it.
How long will it take for my business to get up to speed on this cybersecurity plan?
Knowing the exact amount of time it will take to update or create a plan will help your business assign this task to the right resources.
Estimating time for this project will also help your business ensure that this plan makes it to the top of the list of priorities.
Need help creating your Cybersecurity Plan?
Here at LDI Connect, we know how helpful a solid game plan can address cybersecurity threats. We make sure to assess your current strategy for handling cybersecurity concerns and then work with you to implement and follow a cohesive plan moving forward.
Our team of cybersecurity experts can help you with a wide range of cybersecurity-related concerns. Some of those concerns include finding a ransomware solution that works best for your business and help you decide on which malware software to implement.
If you’re interested in implementing a Cybersecurity plan today, be sure to reach out to one of our specialists.