What is an IT Security Risk Assessment and a Penetration Test?
Consulting Services | IT Professional Services | IT Security Risk Assessment | Managed IT | Network Infrastructure | Network Security & Cybersecurity | Penetration Test
Understanding IT Security Risk Assessments and Penetration Tests can be tricky. The problem is that there are many options that can help protect your company’s critical information and network.
Like a fire alarm system that alerts people of a fire in a burning building, an IT Security Risk Assessment and Penetration Test warns your company of any security gaps, assets, and threats.
Our Managed IT department at LDI Connect can provide an end-to-end assessment of your security landscape by first assessing your security posture and then conducting a penetration test to identify what your IT infrastructure looks like from a hacker’s perspective.
How can you tell the difference between an IT Security Risk Assessment and a Penetration Test? In this article, we will define both, and we will also break down the reasons you might perform them. After reading this article, you will have a better idea of which your company may need
Let’s dive into defining what an IT Security Risk Assessment and Penetration Test is and does.
What is an IT Security Risk Assessment, and How Does It Work?
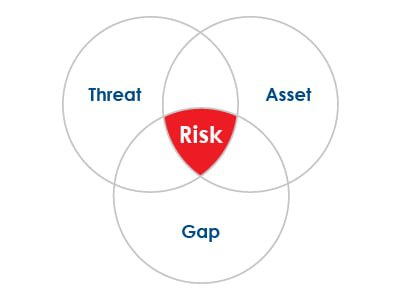
IT Security Risk Assessments identify, assess, and modify risks and data assets within your company’s computer systems, network, and overall IT infrastructure. These assessments can create risk profiles for each data asset and determine what information each asset stores and how sensitive the information is. An assessment will also check a data asset’s impact on revenue and exploitation of the company.
An IT Security Risk Assessment prioritizes ranked risks. It applies mitigating controls for each risk depending on the results of the assessment.
Finally, an IT Security Risk Assessment allows internal personnel to view and collaborate on the organization’s security posture.
Knowledge is power. Assessing your company’s valuable information and vulnerabilities puts you a step ahead of a hacker looking to access your sensitive data.
After conducting an assessment, implementing a cybersecurity plan is paramount in preparing for any alleged cyberattack. Your company’s steps towards a more secure IT infrastructure can help your employees feel more like their information is being protected, but you will also help your customers feel safe working with you.
What is a Penetration Test, and How Does It Work?
 A Penetration Test assesses your computer system’s applications for vulnerabilities and susceptibility to various threats. A penetration test acts as an authorized cyberattack on your IT infrastructure. By essentially attacking your own IT infrastructure, you will get a firsthand view of what security precautions a hacker could find and break through.
A Penetration Test assesses your computer system’s applications for vulnerabilities and susceptibility to various threats. A penetration test acts as an authorized cyberattack on your IT infrastructure. By essentially attacking your own IT infrastructure, you will get a firsthand view of what security precautions a hacker could find and break through.
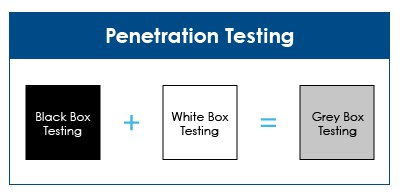
Within penetration testing lies three forms of testing:
White- Box Testing:
White-Box Testing dives into the internal structure and works on fixing the software’s source code. Before white-box testing, testers are provided with the user information needed to access your company’s data. They then proceed to attack your company’s system using that information.
Types of white-box testing include unit testing which tests an application on each unit or block of code as it is being developed and tested for memory leaks, which involves searching for causes of slower running applications.
Black-Box Testing
Black-Box Testing ensures that all interface functionality works well. Black-Box Testers are given little to no information before conducting an ethical hacking and breaking into an environment.
Types of Black-Box Testing include functional testing, non-functional testing, and regression testing. Functional testing involves software testing related to the functional requirements, whereas Non-Functional testing involves testing performance, scalability, and usability.
Regression Testing involves checking to see if any newly developed code has affected any existing code after any type of system maintenance occurs.
Grey-Box Testing
Gray-Box Testing involves using both forms of testing simultaneously in a non-intrusive manner. Non-intrusive testing means using extra hardware that can gather timing or processing information.
Through Gray-Box Testing, you are focusing on all layers of your complex computer system, and you will be able to see context-specific issues that correlate to every web system.
Why is Implementing an IT Security Risk Assessment and a Penetration Test Essential?
An IT Security Risk Assessment and a Penetration Test can help assess your company’s security risks and test your IT infrastructure.
Let’s take a deeper look at why implementing an IT Security Risk Assessment and a Penetration Test are important.
Identifies Critical Security Vulnerabilities
Both an IT Security Risk Assessment and Penetration Test can help your business assess its vulnerabilities before cyber attackers do. Learning what security gaps, risks, and assets your company has will help your company understand what security measures need to be put in place moving forward.
Some vulnerabilities include applications that need to be security patched or systems that need to be hardened with encryptions.
Assesses The Damage
A Penetration Test can help your company recognize the potential damage a successful attack would look like on your IT infrastructure.
Penetration testing provides a real-world overview of exactly what data can be accessed if your organization’s network went through a data breach. Through this testing process, you’ll be more aware of vulnerabilities that cannot be detected during an IT Security Risk Assessment—for example, figuring out whether sensitive information can be accessed while in transit.
Penetration testing gives your organization a leg up on what could happen when faced with a threat and can ultimately save you a lot of stress and money in the long-run.
Which is Right For You?
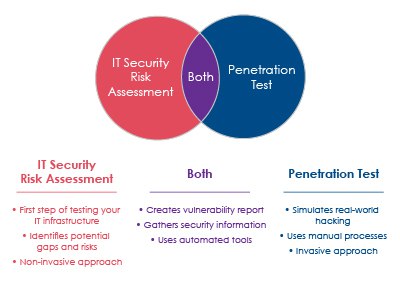 We covered what an IT Security Risk Assessment and a Penetration Test is. We also went over how both can benefit your company.
We covered what an IT Security Risk Assessment and a Penetration Test is. We also went over how both can benefit your company.
At this point, you may be wondering – does my company need one of them or both? The truth is, every company can benefit from being over-prepared when it comes to securing their IT infrastructure.
Both an IT Security Risk Assessment and a Penetration Test can help secure your company’s IT infrastructure. Depending on your security goals and needs, your company might only need one or the other.
How Can LDI Connect Help Your Company?
At LDI Connect, our Managed IT department can help you understand what is necessary for your company and what to expect from receiving an assessment. Once we assess your current security posture, our Managed IT department will set your company up with the proper security foundation to properly secure your IT infrastructure.
By setting you up with a free IT Security Risk Assessment, your company will be able to effectively identify your existing security gaps and gauge whether you need more information with a Penetration Test.
Contact us to help you secure your network and computer system today through a one-on-one consultation! If you’re interested in assessing your current security posture, find out more through the link below!