Where Are Printers Most Vulnerable?
Cybersecurity Plan | Data Breaches | MPS | Multifunction Printers | Office Copiers, Printers, and MFPs | Print | Print Assessment | Printers | Workflow Automation
Printers introduce security risks that many organizations overlook. These devices store documents, manage credentials, and communicate across your network, which means they can be targeted the same way a computer or server can. Understanding where vulnerabilities appear is the first step in strengthening your print environment.
Printers become vulnerable when they are not configured, monitored, or updated with the same rigor applied to other endpoints. Attackers look for gaps in firmware, authentication, and network pathways because those areas often receive less attention. Identifying these gaps early helps prevent unauthorized access and data exposure.
The key takeaway is that printer security is not optional. It is an essential part of protecting confidential information, maintaining uptime, and preventing misuse of network-connected devices.
Why Printers Are Frequently Targeted
Printers are targeted because they operate as fully connected endpoints. A multifunction printer stores scanned images, holds user address books, caches print jobs, and communicates with cloud and mobile workflows. Each of these capabilities creates a potential attack surface.
Printers also become targets because they often run outdated firmware. When updates are missed, known vulnerabilities stay open and can be exploited easily. Consistent patching helps close these exposures.
Most importantly, printers are attractive to attackers because they are rarely monitored. When a device is connected to the network but not actively watched, malicious activity can occur without being detected.
The Most Common Printer Vulnerabilities
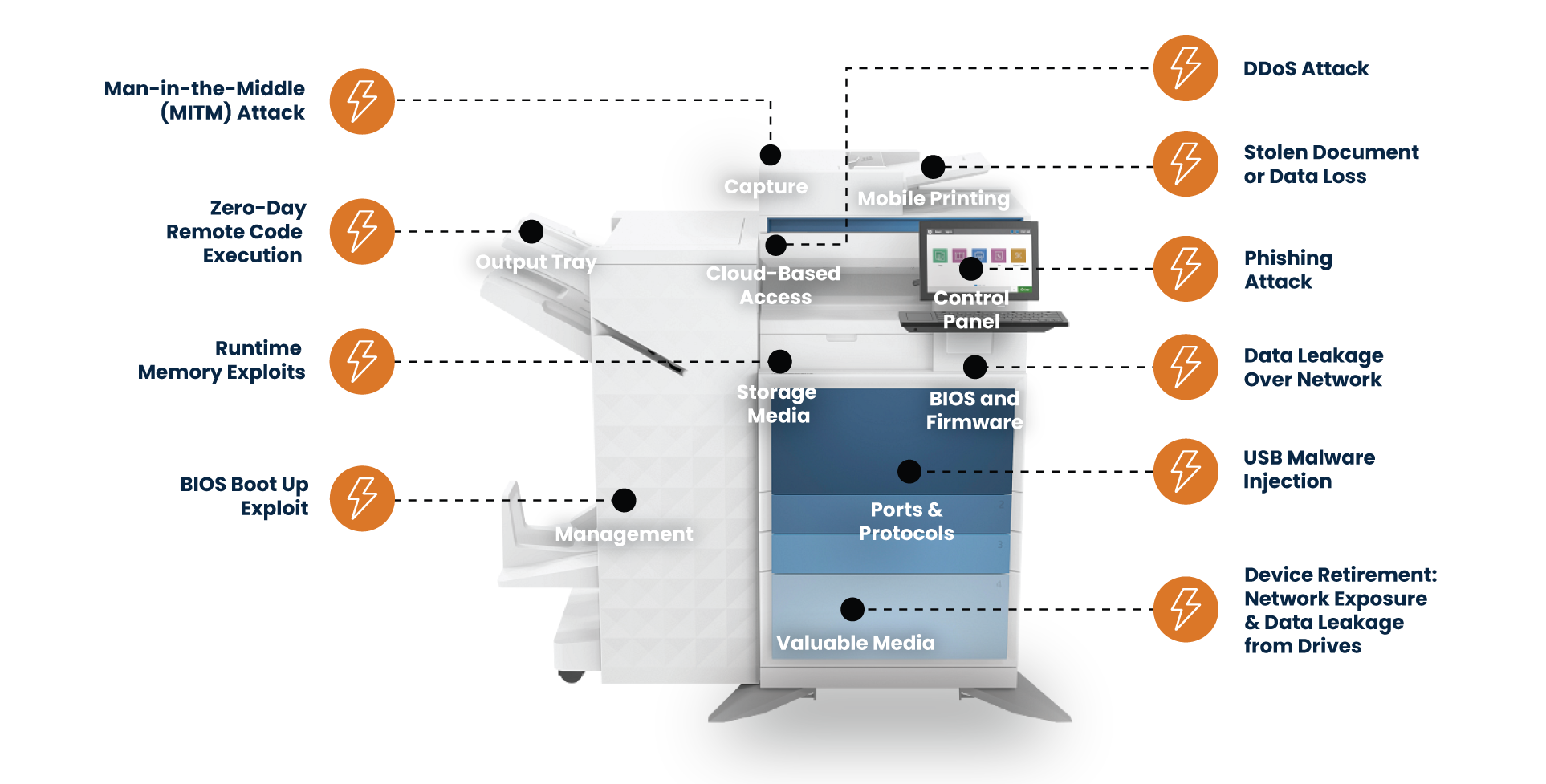
Zero-Day Man-in-the-Middle (MiTM) Attacks
A man-in-the-middle attack occurs when an attacker intercepts print jobs as they travel across the network. During the printer’s “capture” stage, when it receives and queues incoming jobs, the data is briefly exposed, which makes it vulnerable if traffic is not encrypted. Encrypting print streams and enabling secure release features keeps sensitive documents protected while in transit and during capture.
Remote Code Execution
Remote code execution can occur when unpatched firmware allows malicious instructions to run directly on the device. One common entry point is the output tray, where attackers can exploit how the device handles print jobs to inject unauthorized code. Enabling automatic firmware updates closes these vulnerabilities before they can be leveraged.
Memory Exploits
Memory exploits occur when attackers manipulate the printer’s active processes. These attacks take advantage of weak runtime protections. Device hardening and security settings reduce the likelihood of unauthorized access.
Boot-Level Attacks
Boot-level attacks target the printer during startup. When BIOS or system protections are not enabled, malware can embed itself early and operate undetected. Securing the boot sequence prevents persistent threats from being installed.
Device Flooding and DDoS-Style Disruptions
Printers can be overwhelmed by excessive network traffic. When traffic spikes beyond what the device can handle, printing slows or stops entirely. Network controls and traffic limiting settings protect devices from disruption.
Document Theft
Document theft happens when printed materials are left in the output tray or stored digitally on the device. These documents may include confidential information. Secure print release and encrypted storage prevent unauthorized access to sensitive files.
Phishing Through Print Workflows
Phishing can occur when attackers spoof scan-to-email prompts or device notifications that appear on the control panel. The control panel is a trusted touchpoint where users expect to enter credentials, which makes it an ideal place for attackers to imitate system requests. Authentication controls and ongoing user training reduce the success of these tactics.
Unencrypted Data Paths
Unencrypted data paths expose information as it moves between devices. When data is not protected, it can be intercepted and read. Enforcing encrypted protocols ensures information remains private.
USB-Based Malware
USB-based malware becomes a threat when ports are left unrestricted. Attackers can connect removable drives and introduce malicious software directly. Restricting USB access prevents unauthorized devices from interacting with the printer.
End-of-Life Data Exposure
End-of-life exposure occurs when retired printers still contain stored documents, credentials, or configuration data. This information can be recovered if the device is not wiped properly. Securing or destroying internal storage is essential during decommissioning.
Where Vulnerabilities Usually Appear
Printer vulnerabilities usually appear in the same four areas across most models. The first common area is cloud and mobile workflows, which expand convenience but must be secured through authentication and encryption. When these pathways are left open, unauthorized users can access print services.
The second area is the device interface, including the control panel and administrative settings. Open access to these panels can expose stored credentials and critical configuration menus. Restricting access helps prevent misuse.
The third area is ports and network protocols. Devices often ship with legacy protocols enabled by default, and these settings create unnecessary security gaps. Disabling unused protocols reduces exposure quickly.
The fourth area is internal storage. Printers retain digital copies of scanned, copied, and printed materials unless encryption is enabled. Encrypting this storage protects sensitive information.
How to Reduce Print-Related Risks
The key takeaway is that print security requires a layered approach. Device hardening is the first layer because it removes unnecessary access points and enforces authentication on the device itself.
Data encryption is the second layer because it protects both stored data and data traveling across the network. When encryption is enabled, documents remain secure even if intercepted.
Firmware updates form the third layer of protection. Keeping devices updated closes vulnerabilities that attackers frequently target. Updates should be scheduled consistently to maintain security.
Monitoring is the fourth layer. Tracking device behavior helps detect unusual activity early. When monitoring is in place, suspicious events can be addressed before they create disruption.
Secure decommissioning is the final layer. Wiping or destroying storage prevents data from being recovered after the device is retired.
Strengthen Your Print Security with LDI Connect
LDI Connect helps organizations evaluate their print environments, identify vulnerabilities, and apply best-practice security configurations. With more than 25 years supporting secure print and IT infrastructures, the team provides the expertise needed to keep devices protected.
A print security assessment is the easiest way to understand where vulnerabilities exist. Schedule an assessment to begin strengthening your print environment.